The primary benefit of a SIEM system to any organization, is the fact it immensely increases the effectiveness of incident response teams. The early detection of occurrences is a key factor for incident containment and eradication, which means a reduced overall impact.
Since SIEMs can correlate events from different data nodes and devices, this allows for detecting incidents that would otherwise be completely missed. For example, a network intrusion prevention system can usually only see a part of an attack, while the affected host (e.g., a notebook or a server) can see the other part. A SIEM sees the bigger picture by combining logs from both devices, thus making it possible to have a complete picture of the incident.
“A SIEM’s power is in its correlation”
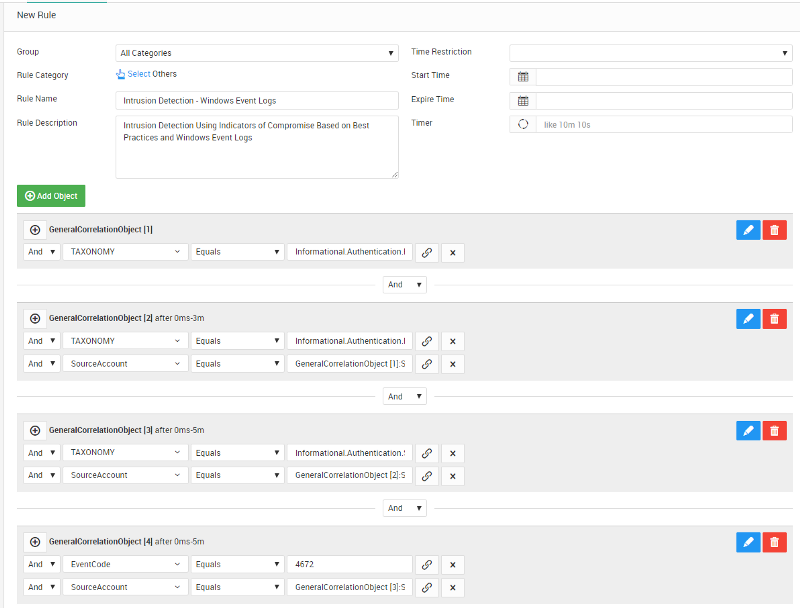
Microsoft Windows® Active Directory best practices consider different signs to identify and evaluate a compromised computer system by correlation, through a proper configuration of Windows auditing settings. These signs can help to detect a malicious activity in a computer system early and timely. The following security events can be considered as part of the correlation to detect possible signs of computer system intrusion within Windows® operating system.
- Two attempts to login as the User were executed.
- User session started successfully.
- Special privileges were assigned to User’s account.
- A new user account was created, named “Jack”.
- A global group with security-disabled settings was created.
- An explorer process has been created.
- An attempt to unregister a security event source was executed.
- Jack’s account was enabled.
- The auditing settings on access-control object were changed.
- Paul’s account session was closed