Intelligence in LOGTITAN SIEM
LOGTITAN is a next-generation SIEM solution with a powerful correlation engine. Its rule based correlation engine with taxonomy has a superior detection capability. Additionally, LOGTITAN has a Machine Learning detection module. What machine learning offers is the ‘many-eyes’ option. With the experienced scientist point of view LOGTITAN has placed its bets on the combination of rule based correlation, human and machine intelligence in its most recent cybersecurity efforts, which reduces the time it takes to detect and respond to cyberattacks. A key differentiator is our unique approach to use machine learning, rule based correlation and human intelligence in parallel. LOGTITAN was designed as a full scope tool that uses machine learning, rule based correlation algorithms and correlation framework for the security specialists to detect emerging threats.
Rule Based Correlation Engine
Rule-based correlation uses traditional correlation logic to analyze collected information in real time. All logs, events, and network flows are correlated together with the power of taxonomy module. Real-time event correlation is all about proactively dealing with threats. Data breaches are on the rise and hackers use highly targeted attacks to intrude upon enterprise networks and steal sensitive data. Protecting your network data from attackers involves detecting security threats at its early stage. Security investigators need to determine whether a suspicious event or chain of security events that had happened on the network is a potential security threat or not.
Manually investigating events across the network from various log sources and correlating them to formulate an attack pattern will be a herculean task for the security investigators.
To effortlessly identify the possible intrusions in the network, you need to have an automated effective correlation engine that gives a complete scope of any security incident by building relationships between events happening across your network infrastructure.
Detection Framework
LOGTITAN SIEM is a security platform which differs from many SIEM products. The main difference is that the correlation engine is rule based plus a framework which you can embed your own logic. There is no restriction in the logic because you can develop your logic in JAVA including Machine learning, statistical methods and artificial intelligence. LOGTITAN is ready for the following libraries also:
Behavior profiling
Automatically classifies and profiles all log and network activity by application, protocol, geography, network location, ports as well as many other categories, and tracks all related traffic statistics. Behavior analysis capabilities can be applied to all data parsed from log sources as this capability enhances rule-based correlation.
Machine Learning
LOGTITAN ML module is a MLLib based Bayesian clustering algorithms to detect threats. MLlib is Spark’s machine learning (ML) library.
The machine learning component of LOGTITAN contains routines for performing suspicious connections analyses on traffic data. These analyses consume a collection of firewall events and produce a list of the events that are considered to be the least probable, and these are consider the most suspicious.
LOGTITAN infers a probabilistic model for the network behavior of each IP address. Each network log entry is assigned an estimated probability (score) by the model. The events with lower scores are flagged as “suspicious” for further analysis.
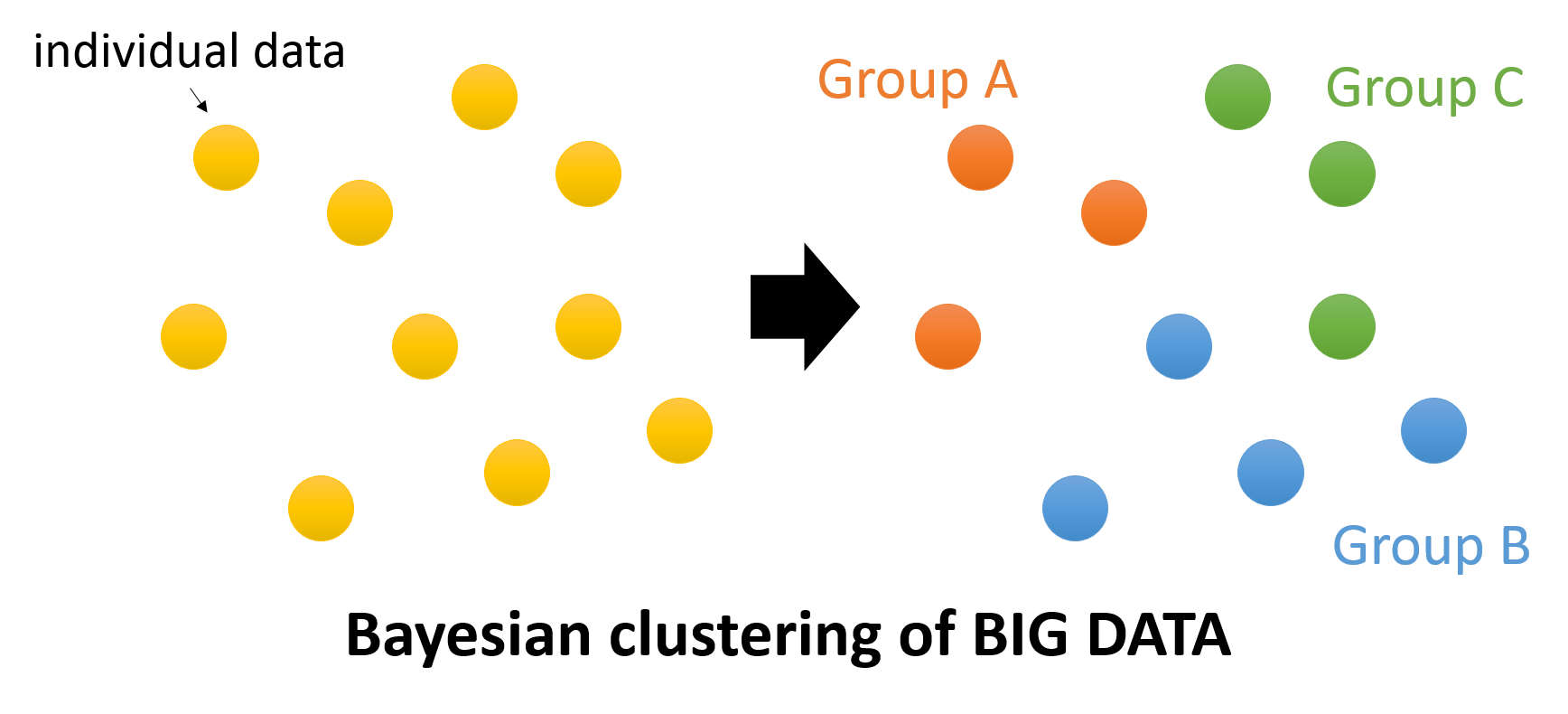
LOGTITAN unique method combining rule based correlation, machine learning and human intelligence amplifies security operations.
LOGTITAN’s scalability and machine learning capabilities support an ML-based applications that can run simultaneously to provide organizations with maximum analytic flexibility.
