Can Cloud SIEM Solutions Satisfy Compliance Regulations?
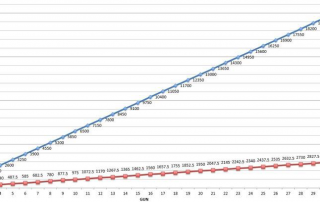
Cloud SIEM are now popular and considered a cheaper solution. There is no software to purchase, cybersecurity professionals to hire or additional training needed to the staff up. But you have to consider log shipping costs, data sensitivity, data sovereignty as potential cons with this approach. There is a [...]