DNS is probably the best source of data for detecting an attacker’s command and control activity, which can be isolated by looking at outbound DNS requests.
Botnets play an important role in malware distribution and they are widely used for spreading malicious activities on the Internet. Identifying algorithmically generated domains in network traffic is a key aspect for analyzing, detecting and mitigating botnet behavior.
A typical form of command and control traffic makes use of domain generation algorithms (DGA) to avoid signature-based detection. Instead of including a hardcoded domain, this type of malware generates new domain names every few days or so, based on the current date. Domain generation algorithms (DGA) are algorithms seen in various families of malware that are used to periodically generate a large number of domain names that can be used as rendezvous points with their command and control servers.
Attackers use DGA so that they can quickly switch the domains that they’re using for the malware attacks. Attackers do this because security software and vendors act quickly to block and take down malicious domains that malware uses. Attackers developed DGA specifically to counter these actions.
Domain Generating Algorithms (DGA) are used by malicious people to help prevent their malware and other services from being taken down by having their software automatically generating and using random domain names which can be unpredictable at the best of times.
DGA detection can be very helpful to detect malware, because if it is possible to detect the usage of a DGA while analyzing the network traffic of a single sample, then it is very likely that the analyzed sample is malicious since DGA is used commonly by malware but not by benign software.
Because DGA are generative and are not a brute-force list of domains, cybersecurity teams cannot simply create a blacklist of domains.
Signature-based detection is not considered an effective measure against DGA because of the rapid changes in the algorithm. In addition to techniques like entropy change, frequency analysis, comparing domain names to lists like Alexa’s Top 1 000 000 sites and analyzing domain creation date LOGTITAN provides extensive detection techniques for behavior analytics using n-gram and machine learning.
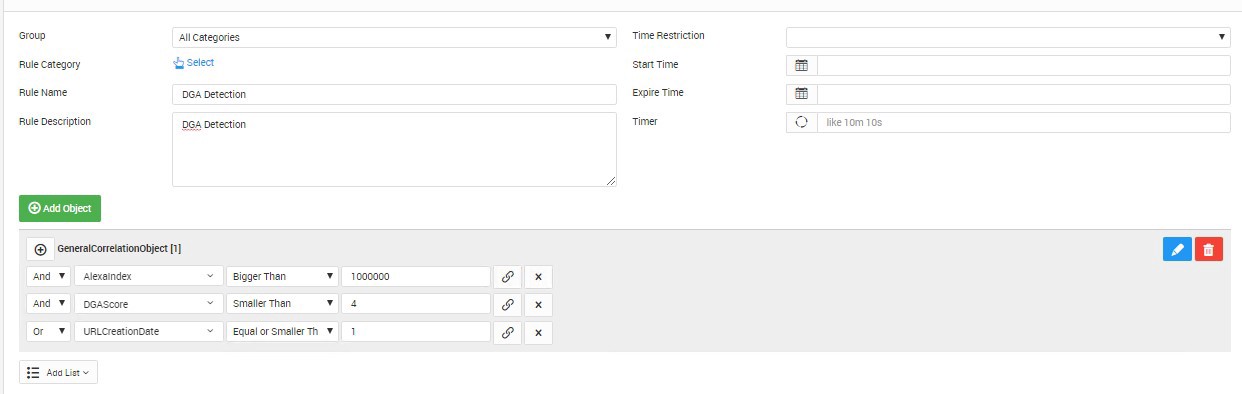
The main advantage of LOGTITAN NGSIEM is that everything is ready in LOGTITAN. You do not have to use complex ML toolkits of your SIEM tools or you do not rely on signature-based solutions like Threat Intelligence and just simple Shannon Entropy calculations.
LOGTITAN uses:
- Entropy change.
- Frequency analysis.
- Comparing domain names to lists like Alexa’s Top 1 000 000 sites.
- Analyzing domain creation date.
- N-gram.
- Machine Learning.
As an end-user, you do not need to be a data science engineer in LOGTITAN NGSIEM. Also, the customer would have to manually configure a threat intelligence feed and the rule to look for DGA on that feed on some of LOGTITAN Competitors. LOGTITAN can detect domains generated by a Domain Generating Algorithm (DGA) using the above techniques automatically.
