How LOGTITAN can help organization to comply with the GDPR.
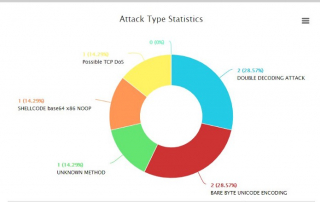
LOGTITAN can play an important role in helping your organization comply with the requirements of the European Union’s looming General Data Protection Regulations (GDPR). We will show you how LOGTITAN SIEM can effectively identify and stop Personally Identifiable Information (PII) breaches. Use Case: Personally Identifiable Information (PII) breached · [...]