LOGTITAN standardizes the category of activities collected from log and machine data.
LOGTITAN has a common taxonomy that provides many advantages. The basic idea here is that LOGTITAN attempt to map various properties of the event into standard taxonomies or classifications.
This feature is more important than parsing since it allows security admins to search for and correlate events across any source using standard terms. For example, a security admin might want to see all authentication events from their firewalls: without taxonomy, this could be extremely difficult — different vendors might have different terms like “login,” “session created,” and so forth to refer to the same basic type of activity, and identifying all the enterprise’s firewalls might itself be a challenge. The analyst doesn’t have to know the exact format of logs for each device. Just search for “Authentication.Success”.
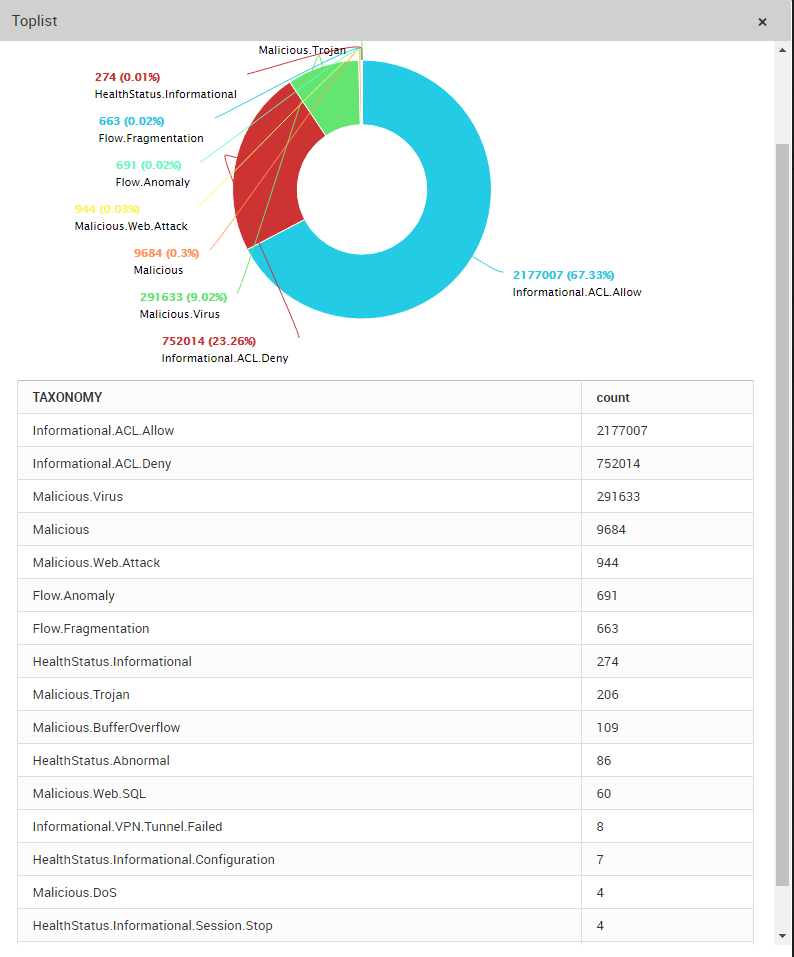 Figure 1. Sample Taxonomy List
Figure 1. Sample Taxonomy List
LOGTITAN utilizes taxonomies to capture trends of activities visually without requiring many searches.
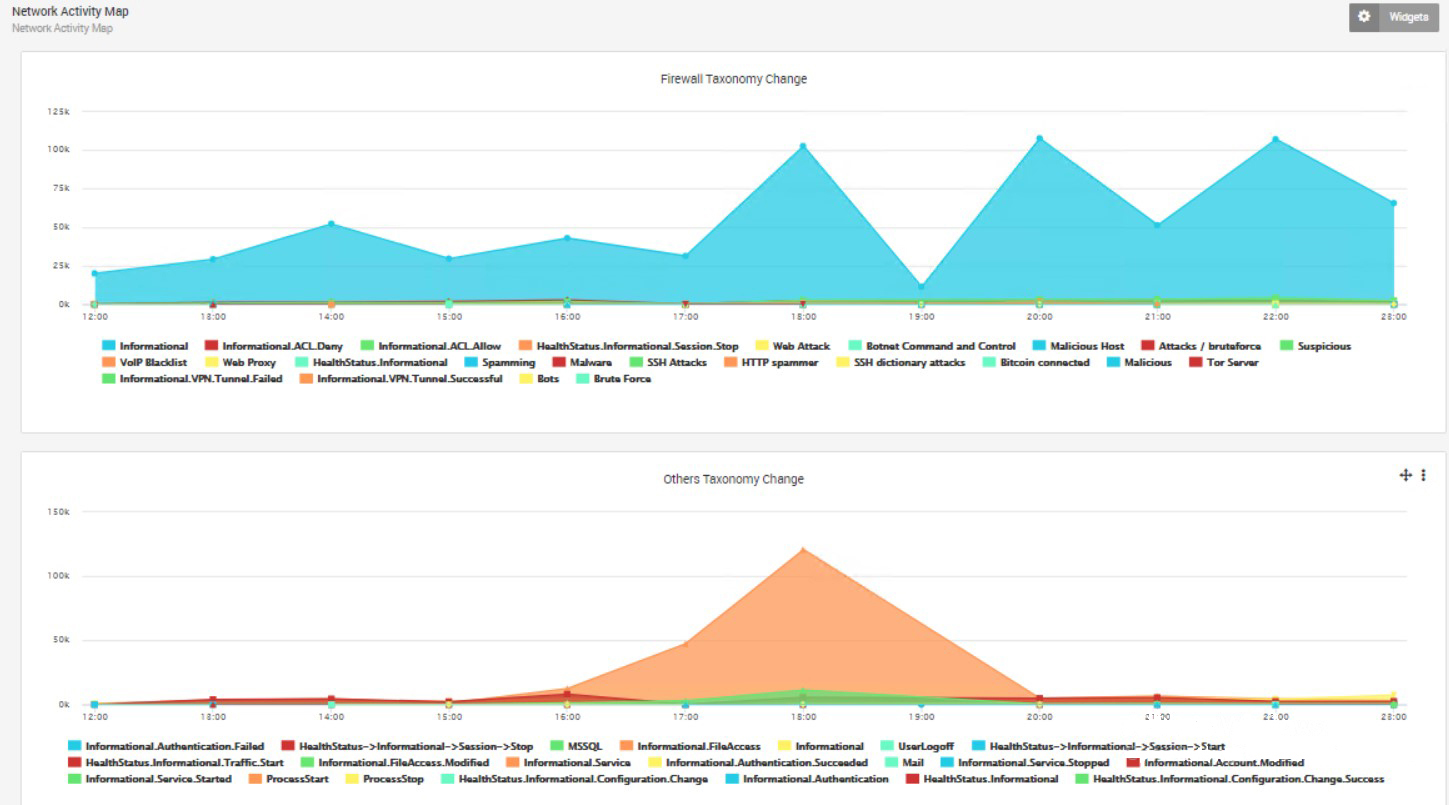 Figure 2. Taxonomy Trends
Figure 2. Taxonomy Trends
