LOGTITAN can play an important role in helping your organization comply with the requirements of the European Union’s looming General Data Protection Regulations (GDPR). We will show you how LOGTITAN SIEM can effectively identify and stop Personally Identifiable Information (PII) breaches.

Use Case: Personally Identifiable Information (PII) breached
· Mr X has username and passwords of various legitimate users of a system
· Mr X wrote a script, that LOGS in the system with user Y credentials and take out his/her PII
· Mr X using known username and passwords extract DATA from the system
· Data was circulated in the student community by the hacker
· Student council informed IT about what happened
For this use case, we will use:
1- Authentication logs from all the log sources, especially servers and ORACLE, MSSQL databases.
With LOGTITAN SIEM, security admins have two detection options.
1. Correlation
2. Log investigation.
Correlation
Use Case steps:
1- Create a list [PII Monitoring List]. Add the username and the corresponding IPs (maybe more than one IP) which this user uses.
2- Check all the authentication request from this [PII Monitoring List].
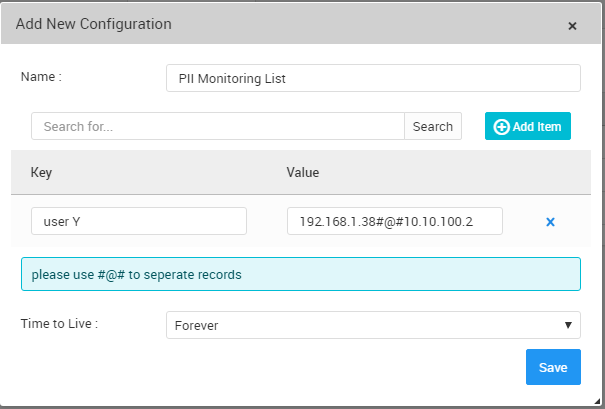
PII Monitoring List
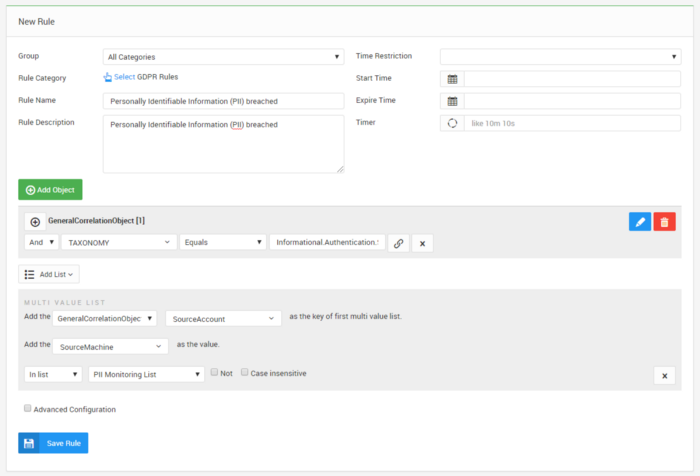
Authentication control rule
Log Investigation
1. Look for user Y login times.
2. Look for the Source IP of this login action.
3. If this IP is not the usual IP of user Y, this is the machine which is running a script.
Additional Notes:
LOGTITAN has predefined correlation rules for detecting Personally Identifiable Information (PII) breaches.