A popular technique for hiding malware running on operating systems is to give it a name that’s confusingly similar to a legitimate operating system process, preferably one that is always present on all systems. Processes whose names are confusingly similar to those of critical system processes are likely to be malicious. Malicious process detection using process name is critical.
Each operating system logs a new process creation event. Windows Event 4688 documents each program that is executed, whom the program ran as and the process that started this process.
If you want to monitor all processes in Linux, just monitor /var/log/audit/audit.log file.
LOGTITAN finds malware attempting to hide execution by running with names that are confusingly similar to legitimate system processes in real-time.
LOGTIAN’s goal is to detect malicious processes that may be hidden between legitimate processes. There is a need to devise a technique that can help digital forensic investigators to discover such similar processes and automate the task. Of course, it must reduce the time needed for the digital forensic investigation process.
Many malware specimens, such as worms, viruses, bots, key loggers, and Trojans, once executed, will often manifest on the subject system as a process. As attackers will most likely want to maintain control of an infected system without being detected, they will look to achieve stealth by camouflaging the name of their malware process to appear as a benign or ambiguous process name, such as “scvhost.” As a result, mere identification of a process without deeper inspection is insufficient.
As a real-time detection, an investigator will want to collect certain information pertaining to each running process to gain process context or a full perspective about the process and how it relates to the system state as well as to other artifacts collected from the system.
LOGTITAN can help an examiner to detect malicious processes. LOGTITAN compares the name of the running process with the legal names of processes.
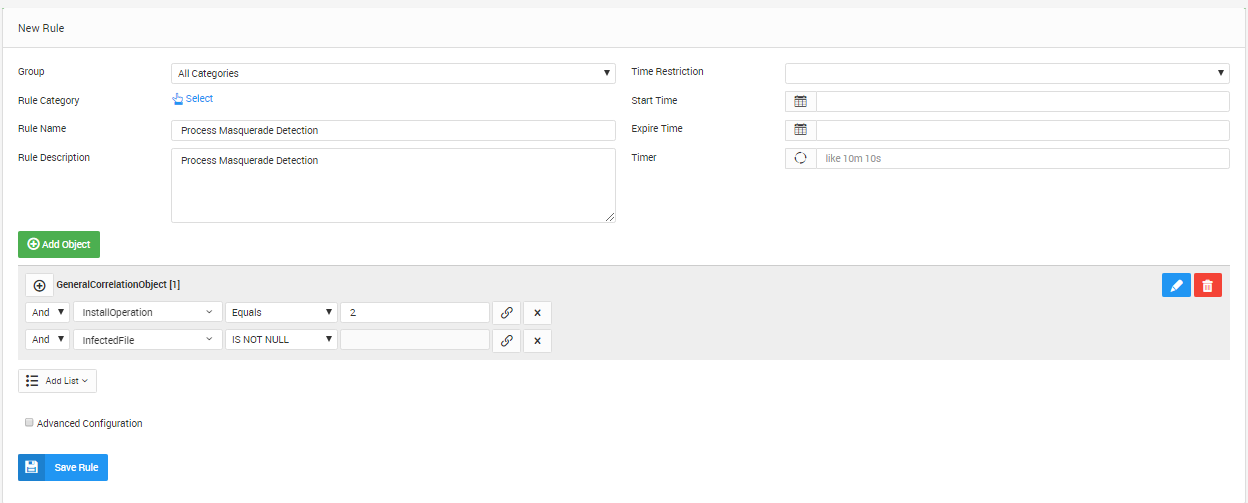
LOGTITAN detects in real-time if there are any malicious processes in the system. Detected malicious processes will be written to “Servingprocess” and the original file will be “Infectedfile” field, and “Installoperation” will set to 2.
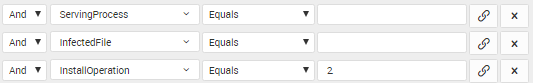
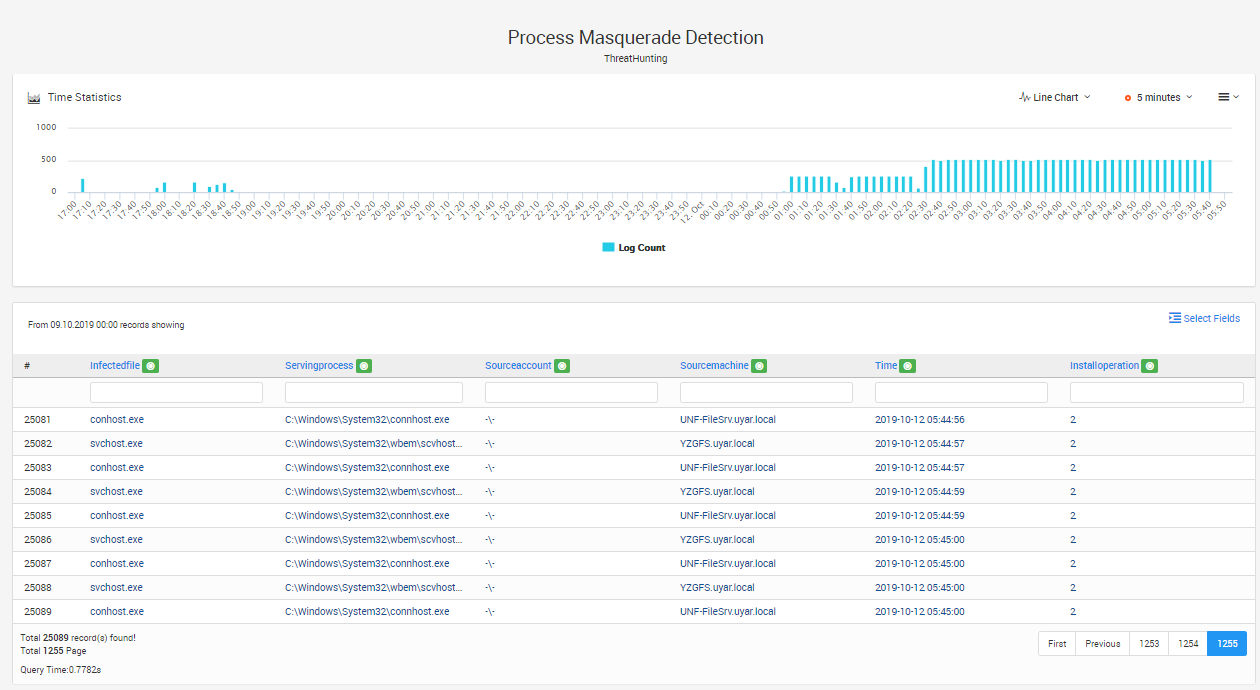
Figure 1. Process Masquerade Detection Reports
There is also a correlation rule to detect process masquerade in real-time. LOGTITAN creates alerts and takes action if process masquerade detected.