
Hundreds of supported data sources plus embedded file integrity monitoring delivers rich information for intelligent monitoring.

Over 700 expert-developed rules churn through data in real-time to pinpoint potential security incidents.
Active response can be configured to automatically quarantine, block, or temporarily disable suspicious activity.

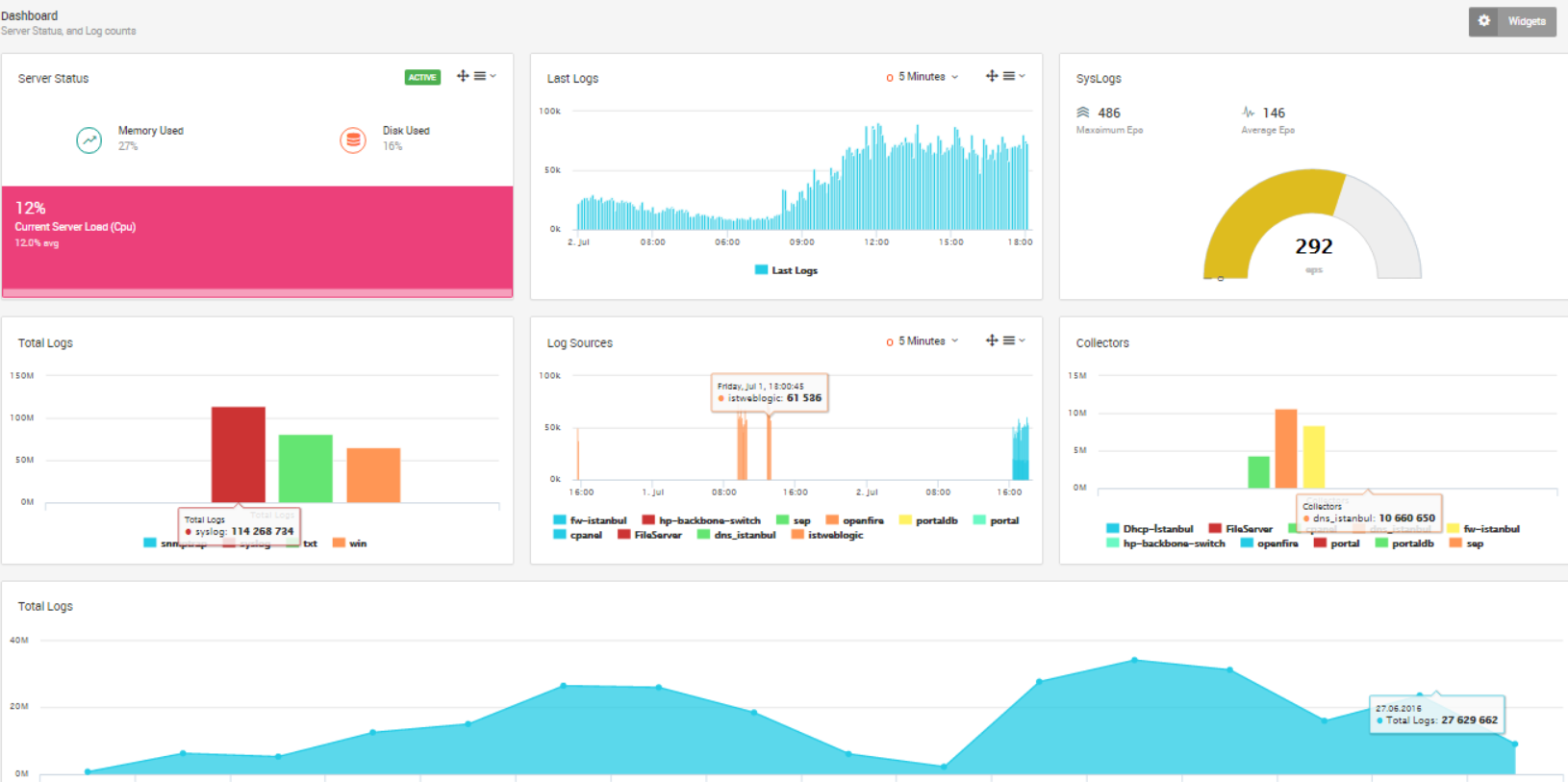
Intuitive dashboards for event and log analysis plus rapid search enable security pros to quickly assess incidents.
Built-in intelligence across networks, applications, and security speeds up root cause analysis.

In-Memory Event Correlation
Access to true real-time log and event correlation by processing log data before it is written to the database, enabling you to immediately respond to security threats and vital network issues with LOGTITAN event correlation feature.
Instantly detect security, operational, and compliance issues, including external breaches, insider abuse, policy violations, application availability, performance problems, and more.
Get alerted in real time and contain threats at network speed.
Leverage over 300 built-in event correlation rules for out-of-the-box visibility and intelligence.
Gain immediate insight into network anomalies and suspicious patterns in your environment.
Detect and stop zero-day, multi-vector and blended threats.
Event correlation is key to an effective SIEM solution. But, not all correlation engines are built equally. With LOGTITAN, you get true, real-time in-memory event correlation to instantly detect and mitigate threats. LOGTITAN is a log analysis tool which provides immediate incident awareness and actionable intelligence so you can respond to vital issues at network speed.
LOGTITAN’s real-time analysis means you’re able to instantly take action to contain a threat or thwart an attack. Moreover, Logtitan provides automated, active responses for hands-free threat mitigation, so you can safeguard your network 24×7.
LOGTITAN enables you to effectively troubleshoot both security and operational issues—be it a data breach or a network performance problem—by understanding the relationship between different activities using multiple event correlations. For instance, an unauthorized application gets installed then a significant increase in FTP traffic is seen going in and out of that system.
LOGTITAN also has the unique ability to set independent thresholds for activity per event, or group of events. By combining LOGTITAN’s powerful correlation and thresholding abilities, you get security intelligence you can count on and reduce false positives.
And, with over 300 built-in event correlation rules and easy-to-understand categorization, LOGTITAN delivers visibility and control right out of the box. Correlation’s library of configurable pre-built rules, along with the ability to create advanced rules with easy rule editor, means you can say goodbye to writing complex scripts to correlate events—eliminating hours of work for you.
Simplify IT Compliance and Regulatory Audit with LOGTITAN
LOGTITAN enables you to effectively manage the impact of compliance risk on your organization. Clients can track regulatory change, manage associated policies and controls.
An effective monitoring program implemented with LOGTITAN addresses compliance gaps, demonstrates risk management, and automates compliance reporting
Compliance audits are quickly evolving from checklist-based to risk-based. To address this increased scrutiny, organizations must demonstrate a strong security focus while at the same time address time-consuming compliance reporting requirements. LOGTITAN helps regulated organizations get the reporting automation they need while providing an all-in-one event and log monitoring, investigation, and incident-response system that supports risk-based monitoring.
Produce Compliance reports in a few clicks with audit-proven template for PCI DSS, HIPAA, FSMA, SOX, ISO 27001 and more.
Easily customize dashboards, rules, and actions to regulated and sensitive systems for effective demonstration of risk management.
Embedded file integrity monitoring & SQL database monitoring fulfill compliance requirements and adds intelligence to the monitoring process.
Active response and USB defender help avoid data breaches and regulatory scrutiny through stopping potential attacks in progress.
The Fastest EPS Performance on the Market
A security information and event management application is only as good as the amount of information it can process in real-time. LOGTITAN gives you the fastest events per second (EPS) logging available today, so you can identify threats as they occur.
Fast EPS performance is also critical to maintaining compliance with ISO 9002 standards as well as SOX, HIPAA, PCI and other federal regulations for online security. Your data will stay safe, you’ll be protected from liability, and you’ll be ready for surprise audits whenever they occur
